Cyber security is a crucial aspect in our increasingly digitized world, and social engineering attacks are one of the most common forms of attacks. One social engineering technique bad actors deploy is impersonation – pretending to be someone other than they actually are. This article sheds light on various forms of impersonation attacks such as phishing, spam, spear phishing, whaling, water holing and fishing.

These attacks aim to manipulate individuals into divulging sensitive information, like credit card or social security numbers, or perform actions that aid the attacker. Understanding how social engineering works, why we fall for it and how to defend ourselves are crucial steps in protecting ourselves from these attacks. In a half-day training, Learning Tree can help you ensure data security on computers, mobile devices, networks, the Internet, and the cloud, regardless of experience level. This article aims to educate individuals and companies about the dangers of social engineering and how to recognize and resist these attacks.
Social Engineering is perhaps the most common attack on physical and cyber security. Seriously, how many bad actors would admit who they really are?
What is Social Engineering?
One definition from Kaspersky is, “Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables.” Another from CMU is, “Social engineering is the tactic of manipulating, influencing, or deceiving a victim to gain control over a computer system, or to steal personal and financial information." But, again, note the focus on manipulation. The idea is to get someone to do something they would not likely ordinarily do or to do something to aid a bad actor.
Motion pictures and television shows often glorify the social engineering activities of grifters and con-men in shows such as the “Oceans” series of movies or the “Leverage” television series. In the cyber security context, social engineers fall into the category of bad actors.
Impersonation as a Social Engineering Tool
If I pretend to be your bank and tell you that you have overdrawn your account, you would be interested in getting more information. The more convincing I am, the more likely you are to believe me. On the other hand, if I phoned and said I was some bank in which you didn't have an account, you'd unlikely believe me. You'd be more trusting if I named your actual bank and gave your account number and mailing address. Most bad actor impersonations are somewhere along that spectrum, however.
In fiction, the impersonators often have extensive resources with which to discover the more personal details, but that’s rarer in real life. Part of the issue is that bad actor impersonators tend to rely more on volume than targeting: they contact thousands of prospective victims and hope to get a small "success" rate. The fictional ones tend to target a minimal number of "marks."
Some Impersonation Types
Multiple, mostly similar, activities fall under the umbrella of types of social engineering activities undertaken by bad actors.
Phishing
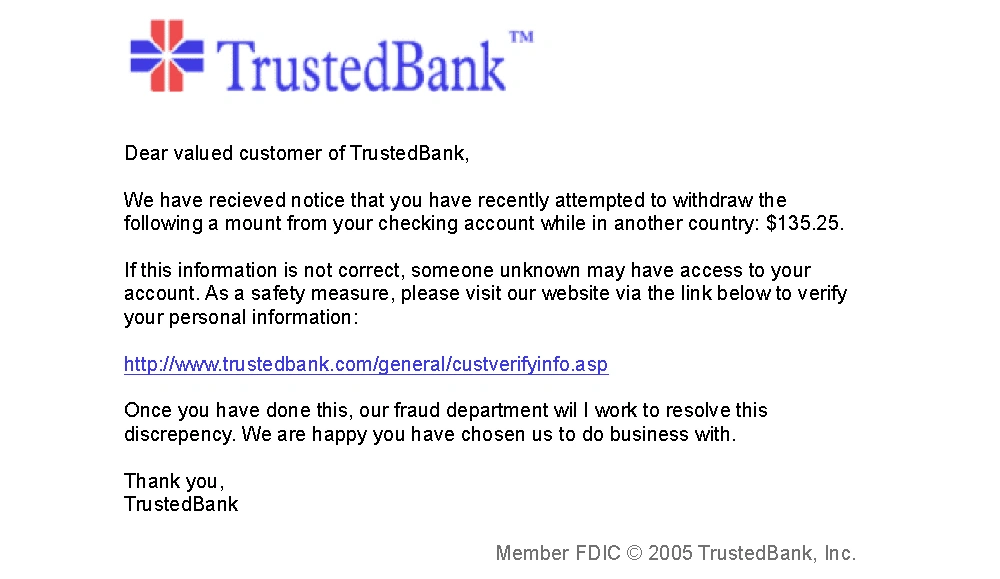
Many people use the term “phishing” to refer to all the techniques in this area. While many are phishing variants, that's only sometimes true for all. One definition of a phishing attack is "… an email fraud method in which the perpetrator sends out legitimate-looking email in an attempt to gather personal and financial information from Recipients". For example, that bogus bank overdraft email from an unknown bank — is phishing.
Spam
Spam (which is not the food item!) is an article or advertisement posted to a website, social media group, or another forum that is usually off-topic and possibly too good to be true. The links in Spam messages may link to bogus websites or invoke other attacks.
SPIM
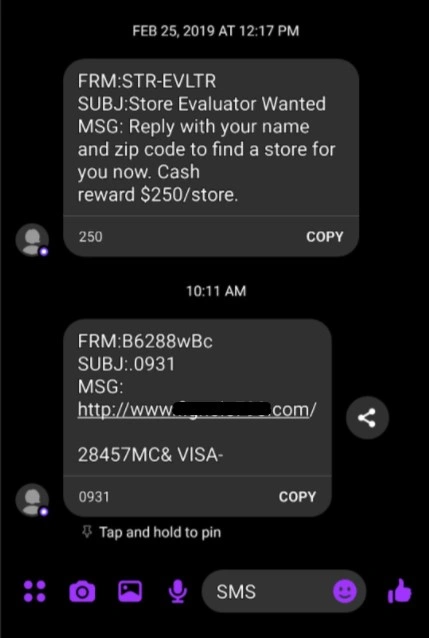
SPIM is unwanted IMs, like email spam. They have bad links or try to trick you into giving personal info. These can come via text message, Facebook Messenger, or other popular social media platforms.
Spear phishing
Spear phishing targets an individual or small group. Because of the smaller number of targets, bad actors can do more research on potential victims. The attackers often research their target on social media platforms, sites of professional societies, and press articles the mark. This is one reason companies discourage employees from sharing personal and business information on the Web.
Whaling
Whaling is a form of spear phishing targeting high-value individuals. Some such targets are considered less vigilant, and the potential reward is much higher, reducing the risk of doing extensive research.
Water holing
"Companies cannot expect employees to know about and remember the steps they should take to help ensure a cyber-safe workplace. Diligence is essential."
Water holing or a water hole attack is a form of targeting. Victims are chosen based on the use of a particular site or business.
Vishing
Vishing uses voice telephone calls to contact the targets.
How it Works
The idea is to get the mark to take some action: click on a link, respond to an email, or (such as in vishing) give information directly to the caller. Unfortunately, links often point to bogus malicious websites designed to look like real ones. Sometimes, the URL is even crafted with a character set that looks like the one for the real set but uses different characters. These sites then solicit personal or company information or try to infect the victim’s computer with malware such as a virus.
Why do we fall for social engineering techniques?
Bad actors may use psychological tactics such as building rapport, using flattery, or creating a sense of urgency to convince a mark to divulge sensitive information or perform actions. All ways that aid the attacker. This type of manipulation can be difficult to detect and defend against. It often relies on exploiting human emotions and motivations. Like a message from your bank that you've overdrawn. It is important to be aware of these tactics and to take steps to educate yourself and others about how to recognize and resist psychological manipulation in the context of social engineering attacks.
How to Defend Yourself
Don't click on links in unsolicited emails, and don't give out information to callers you don't know. The problem is that many users are busy and don't stop to think about this. One of the most important steps companies can take to prevent these attacks is to educate their employees about the dangers of social engineering and how to recognize it. That's why it is essential for companies to have proper security awareness training for all employees of all levels. This is especially important when employees work from home or use personally-owned devices to work. Companies cannot expect employees to know about and remember the steps they should take to help ensure a cyber-safe workplace. Diligence is essential.
Other measures companies can implement include using anti-virus software, firewalls, and monitoring systems to detect and prevent attacks. Additionally, implementing multi-factor authentication can add an extra layer of security to protect sensitive information. By taking these steps, companies can reduce the risk of falling victim to a social engineering attack.
By understanding the different forms of impersonation attacks, such as phishing and whaling, and by recognizing the tactics used by bad actors, individuals can take measures to avoid falling victim to these attacks. Education and awareness are key to reducing the risk of social engineering attacks and defending against them. By staying informed and vigilant, we can ensure that scammers don't gain access to our personal and financial information and remain safe in an increasingly digitized world. With the right knowledge and tools, we can confidently navigate the digital world and stay protected from these malicious actors.
Visit our Cybersecurity page to learn about training for yourself and your team!


